Single Sign-On (SSO) user authentication service allows you to access multiple applications with one set of login credentials (e.g. your username and password). SSO reduces the number of times a user needs to log in to different systems, increases security with a more centralized authentication process, and improves the user experience.
SSO reduces the risk of security breaches caused by stolen or weak passwords and provides an easy-to-use and secure way to manage user access. With SSO, you can access multiple applications and systems without having to log in to each separately.
Insider's SSO Solution
Insider offers SSO that enables you to reach Insider's panel Inone via your Identity Provider (IdP) and its authorization system. You can grant/revoke access to your users and/or user groups on your IdP, manage user roles on your IdP, and enforce an automatic logout from Inone when a user logs out of their IdP.
With SSO, you can enhance your panel security. It reduces password fatigue, helps your organization enforce consistent security policies, and monitors user activity across multiple systems and applications.
SSO reduces the time and effort required to access multiple systems and applications and allows your users to focus on their work and complete tasks more efficiently. This overall can increase productivity.
It can also reduce the administrative burden and costs associated with managing multiple user accounts and passwords across different systems and applications. Additionally, SSO can help your organization streamline user onboarding and offboarding processes as it reduces the time and effort required to set up and remove user accounts.
SSO can help your organization to comply with regulatory requirements and industry standards related to identity and access management such as HIPAA, GDPR, and PCI DSS.
Insider's SSO solution uses the SAML 2.0, the latest version of SAML protocol.
This guide aims to explain the following basic concepts about SSO, and the instructions for setup:
- What is SAML?
- What is a Service Provider?
- What is an Identity Provider?
- What is Just-in-Time (JIT) User Provisioning?
- What is SCIM?
- Requirements for SSO setup
- How to set up SSO
- How to set up additional functionalities
- How to log in to Insider with SSO
What is SAML?
SAML (Security Assertion Markup Language) is a protocol widely used to exchange authentication and authorization data between parties, particularly between an identity provider (IdP) and a service provider (SP). Our SSO solution uses the latest version of SAML protocol 2.0.
What is a Service Provider (SP)?
Service providers are the SaaS (Software as a Service) applications that businesses use such as Slack, AWS, Figma, Atlassian etc. Insider is also a service provider for our customers.
What is an Identity Provider (IdP)?
An identity provider provides authentication services to other systems, services, or applications. Some popular IdPs are Microsoft Azure Active Directory (AD), Okta, Jump Cloud, and Ping Identity. An identity provider is responsible for verifying the identity of a user and providing the necessary information to allow them to access the protected resources in the SSO context.
What is Just-in-Time (JIT) User Provisioning?
JIT user provisioning is a method where user accounts are created in a system or an application only when they are needed but not beforehand. In this system, when a user tries to access a system or an application for the first time, the system checks if they already have an existing account. If they do not have one, the system creates a new account and assigns the necessary permissions and access based on their identity and role.
With JIT being a part of the SSO, once users are allowed access from the IdP, their user will be automatically created on Inone when they first sign in with SSO.
What is System for Cross-domain Identity Management (SCIM)?
SCIM is an open standard that automates user identity management in cloud-based services and applications. It allows administrators to manage user identities in multiple systems and applications on their IdP, and simplifies the user provisioning and management process for them.
SCIM allows you to manage users roles on your IdP, and grant or revoke user access. With SCIM being a part of SSO, once users are allowed access from the IdP, their users will be automatically created on Inone when they first sign in with SSO.
Requirements for SSO setup
- You should have the Administrator role on InOne. Refer to User Management for further details.
- You should have administrator access on your IdP.
How to Set Up SSO
To set up SSO, follow these instructions:
1. Go to Inone to navigate to Settings > Inone Settings > Security.
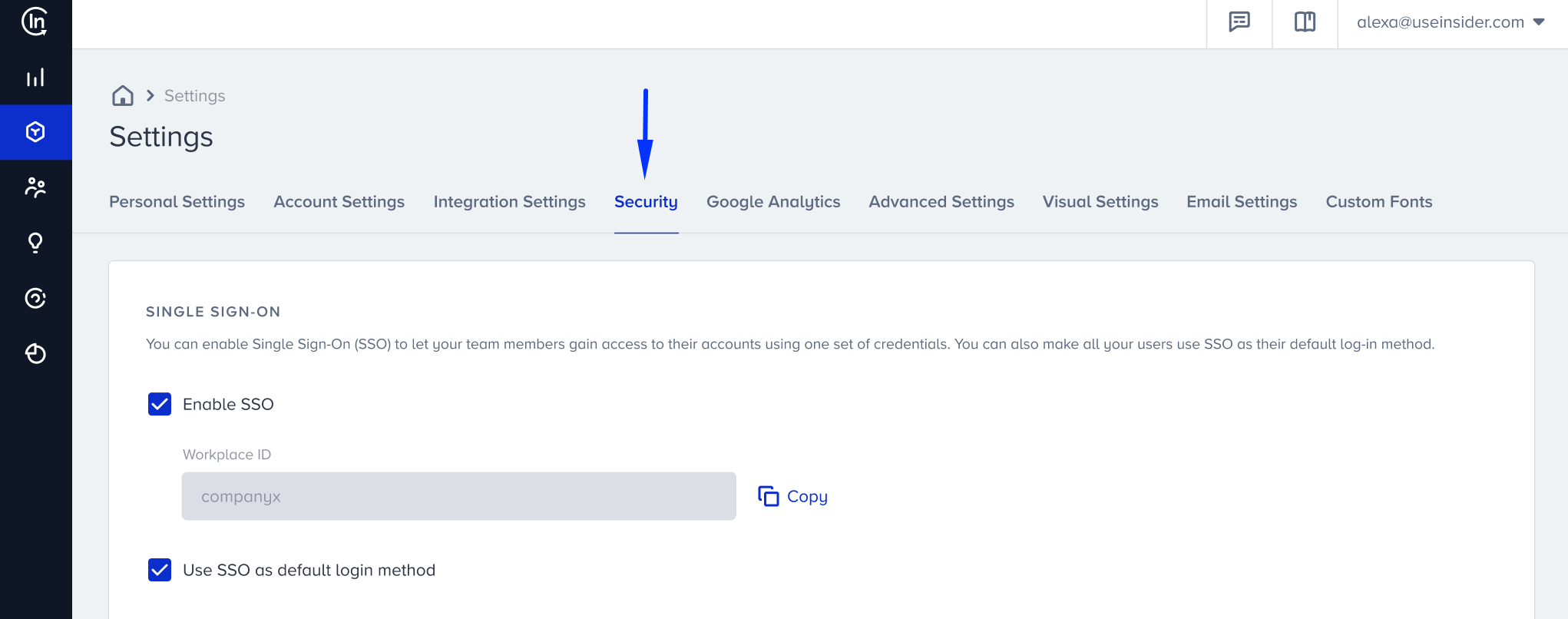
2. Check the "Enable SSO" box. The Workplace ID is the same as your panel name and will be used by users to access the panel when they first sign in with SSO.
3. If you want to enforce all of your users to access the panel via SSO, check the "Use SSO as default login method" box.
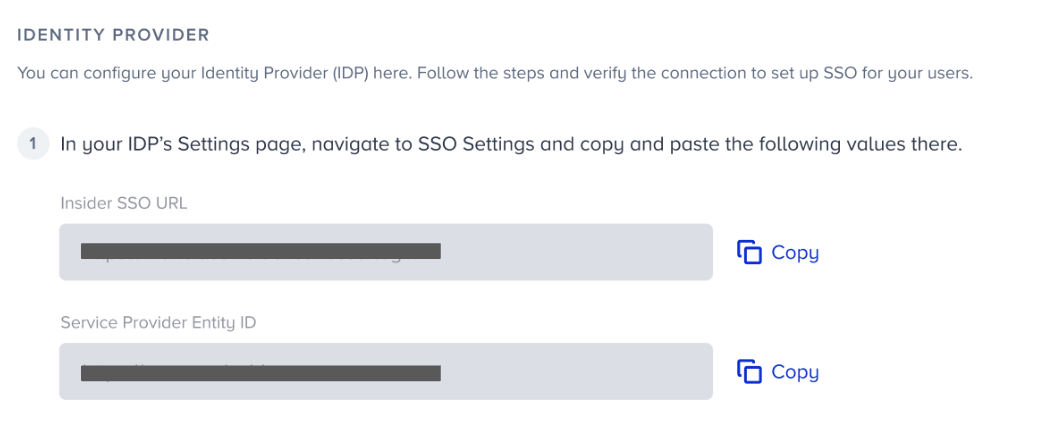
4. Copy the given Insider SSO URL and Service Provider Entity ID, and paste them into the related sections in your IdP.
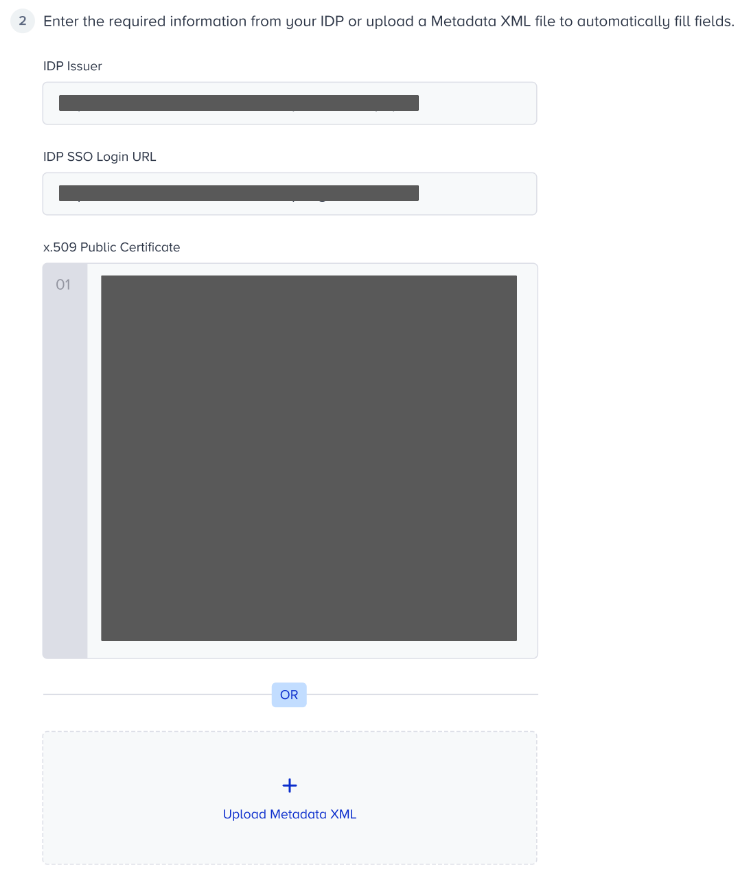
5. Copy the related information from your IdP, and paste it to Insider. You can also use the “Upload Metadata XML” option to upload the file that you obtain from your Idp to populate the input fields automatically.
6. Click the Test SSO Connection button to test your connection. If there is an error, you can see the error code displayed next to the button. Accordingly, you can troubleshoot it and fix it.
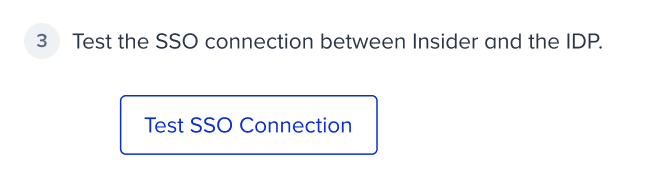
You should pass the SSO connection test to save your settings.
7. Once you pass it, save your settings.
Congrats! You have successfully set up SSO for your users.
How to Set Up Additional Functionalities
You can set up JIT user provisioning, SCIM, and single logout as additional options.
JIT User Provisioning
To set it up, check the "Enable JIT Provisioning" box.

SCIM
To set it up, follow these instructions:
1. Check the "Enable SCIM" box.
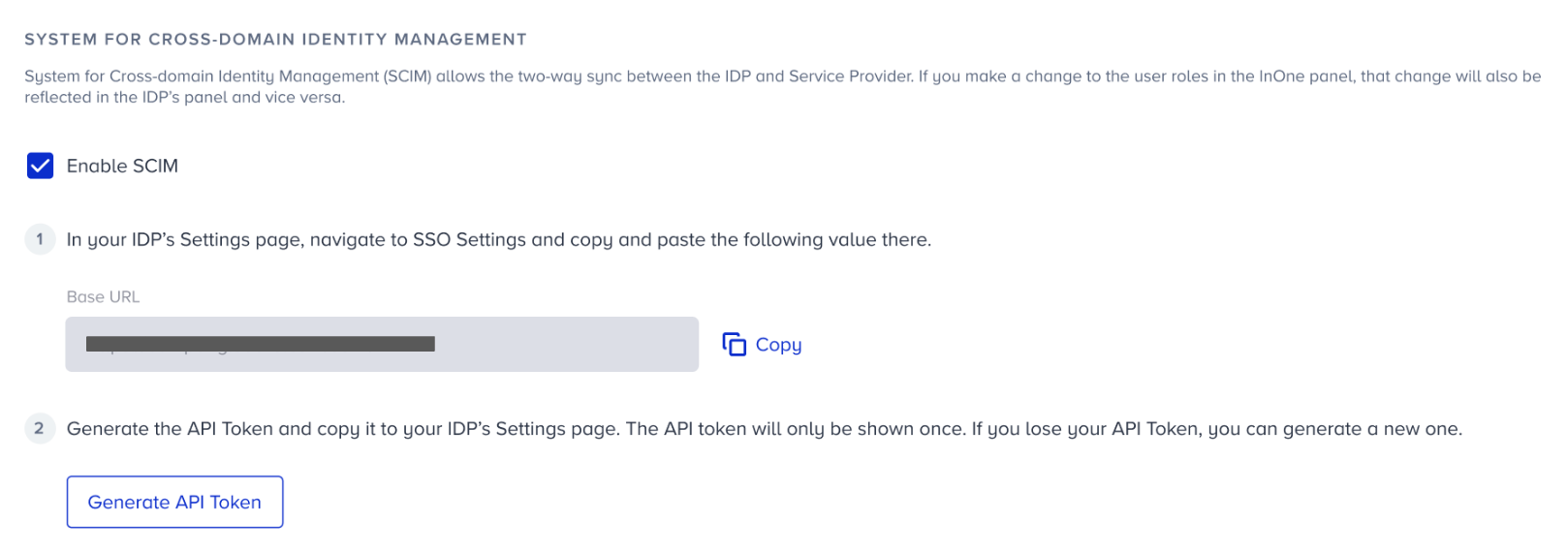
2. Copy the given Base URL and add it to the related section in your IdP.
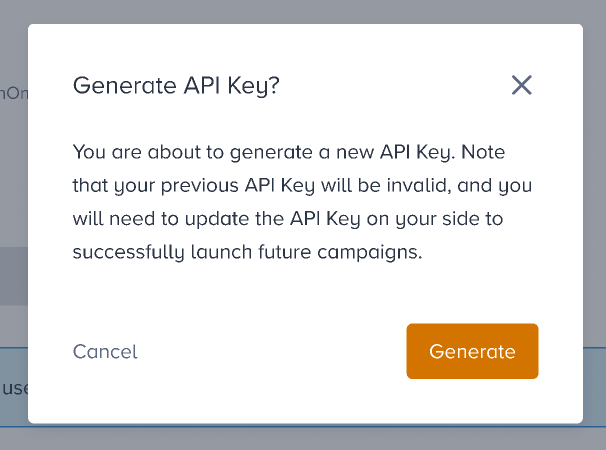
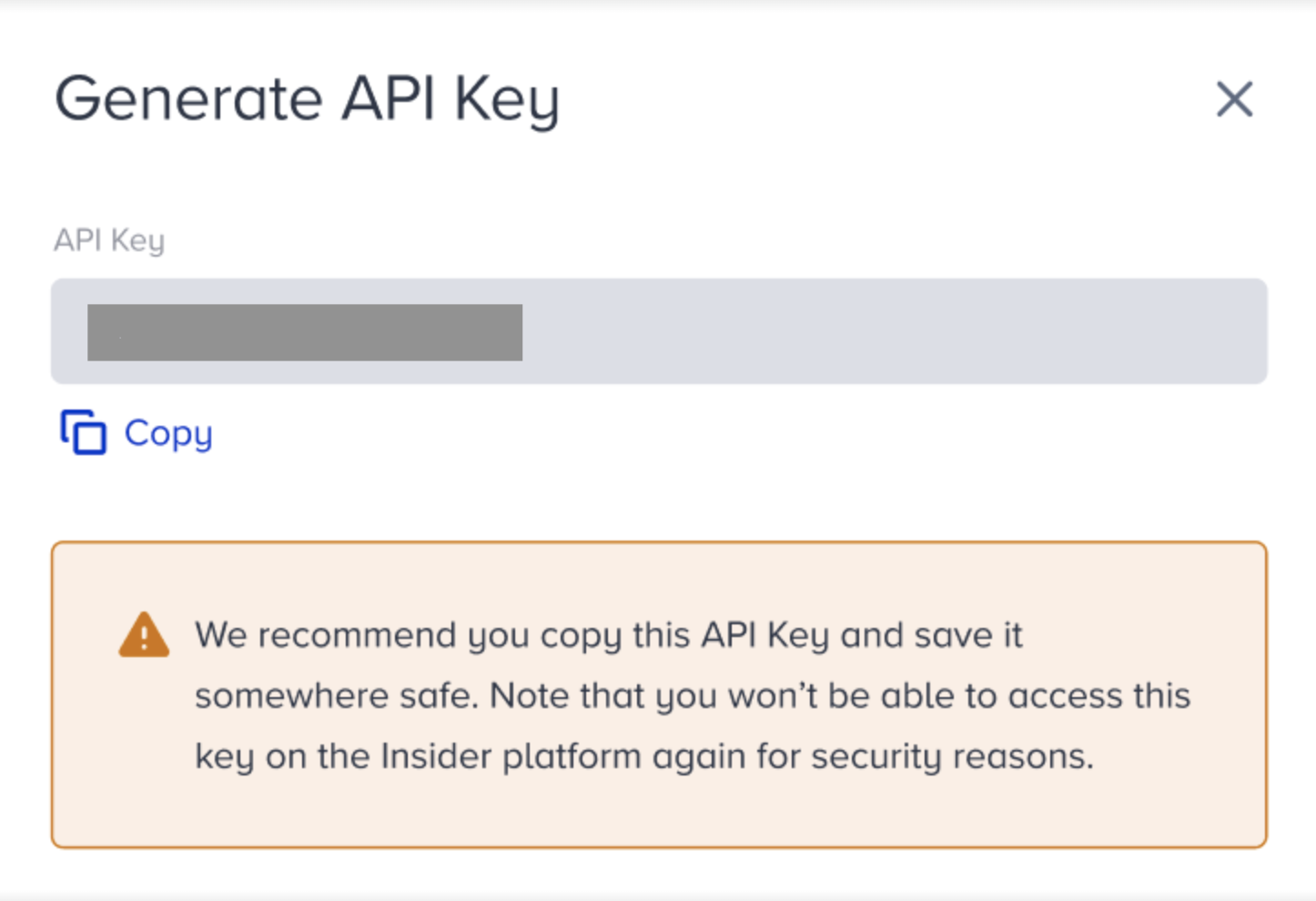
3. Click the Generate API Token button. To access your one-time API token, click the Generate button on the prompt.
4. Enter the generated API token to the related field in your IdP, and save it in case it may be of use in the future.
Single Logout
To set up single logout for your users, follow these instructions:
1. Check the "Enable SLO" box.
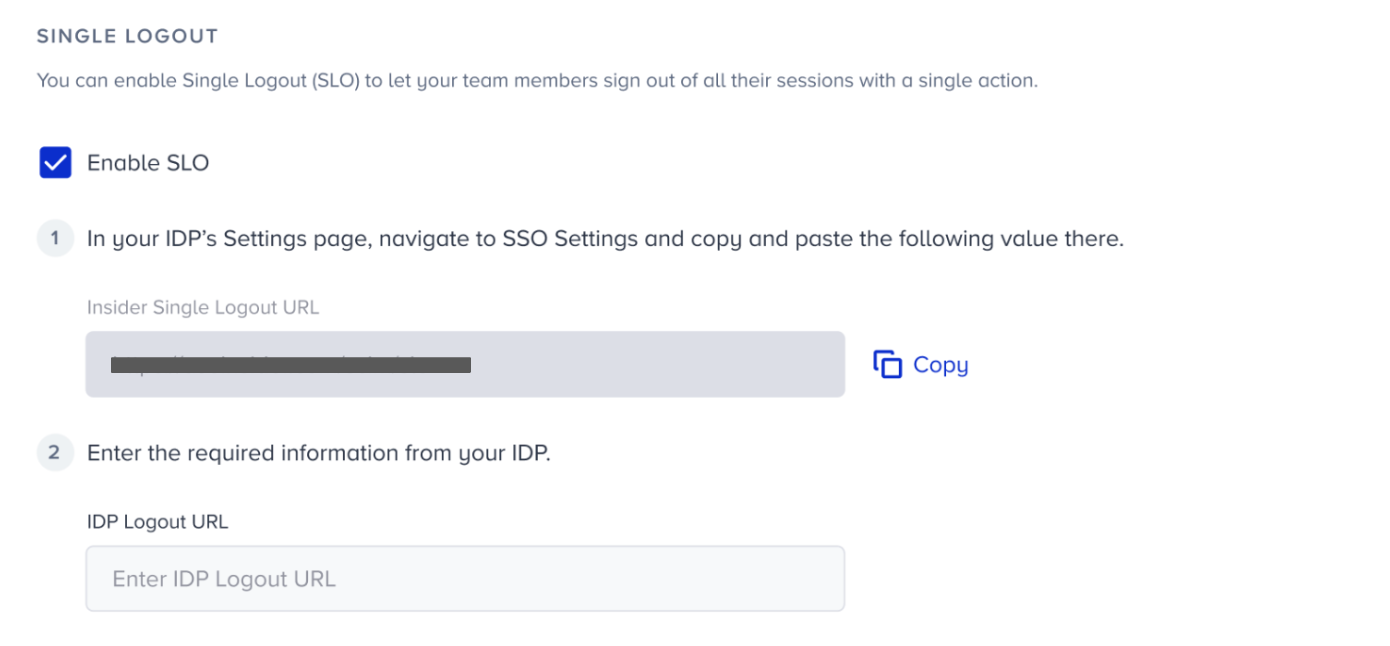
2. Copy the given Insider Single Logout URL, and paste it to the related field in your IdP. Copy the IdP Logout URL given in your IdP, and paste it to the related field on Inone.
How to Log In to Insider with SSO
To log in to Insider with SSO, follow these instructions:
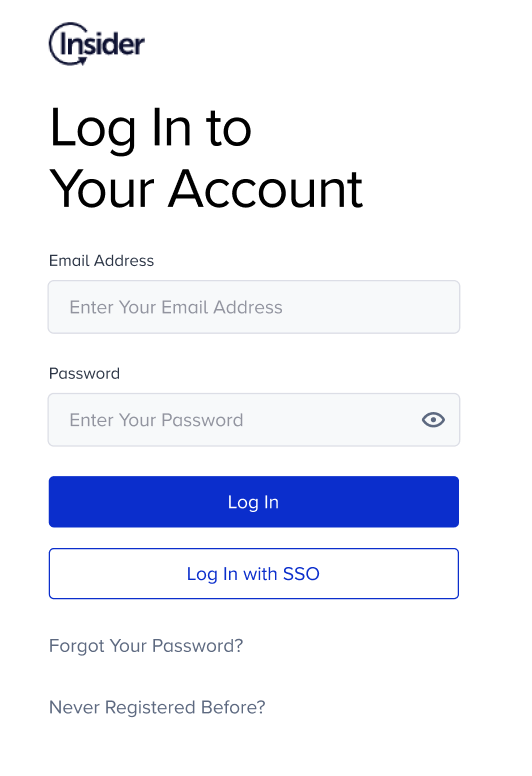
1. Go to the login page of Inone.
2. Click the Log in with SSO button.
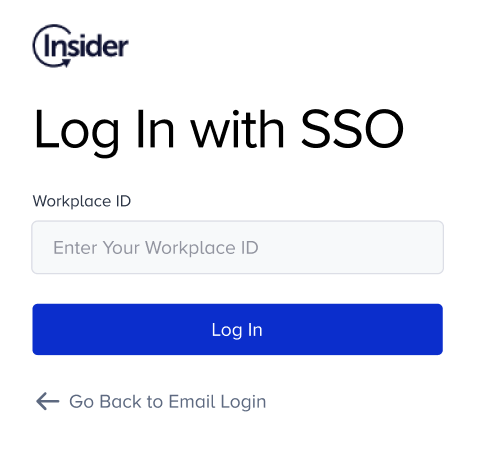
3. Enter your workplace ID. This is the name of the panel you want to access to. You can also see the Workplace ID via Settings > Inone Settings > Security.
4. You will be directed to the IdP login page. Enter your IdP credentials and click the log in button.
Multi-Domain Customers
To set up different user roles for each person for different panels, you have to set up different applications on your IdP for each domain.
For example, User A will have the the Edit & Publish role on the Germany panel and Collaborate role on the France panel, and User B will have the Manage Users role on Japan, Korea, and Singapore panels. Let's say you have five panels and two users only.
In this case, you need to create 5 applications on your IdP, one for each country. You will connect each Insider panel to each application. For example, you should create an application for InsiderFrance on your IdP. Using the information and steps on screen, you should integrate it with the actual Insider France panel. After that, you should create another application for InsiderGermany on IdP, then they will set that one up with your actual Insider Germany panel. At the end, you will see 5 Insider applications on your IdP.
To manage user roles for each panel, you should generate API tokens to set up SCIM as well for each panel. At this point, you can enter any of these applications and set user roles.
Let’s say you enter the Insider Germany application on your IdP, and grant Edit & Publish role to User A. Currently, User A only has access to the Germany panel but not the other panels. Then, you enter the Insider France application and grant access to User A and select the Collaborate role. Now, User A has different user roles in Germany and France panels and no access to Japan, Korea, or Singapore panels.
You can also think User A and User B as Group A and Group B, meaning you can grant access/give user roles to a whole group but not only users.
Benefits of Single Sign-On
- Improved user experience: With SSO, your users only need to remember one set of credentials to access multiple systems and applications. This eliminates the need to repeatedly enter login information and makes the user experience more seamless and convenient.
- Enhanced security: SSO reduces the risk of password fatigue and encourages the use of stronger and more complex passwords to improve security. Additionally, SSO can help your organization to enforce consistent security policies and monitor user activity across multiple systems and applications.
- Increased productivity: SSO reduces the time and effort required to access multiple systems and application to improve productivity, allowing your users to focus on their work and complete tasks more efficiently.
- Cost savings: SSO can reduce the administrative burden and costs associated with managing multiple user accounts and passwords across different systems and applications. Additionally, SSO can help your organization to streamline user onboarding and offboarding processes, reducing the time and effort required to set up and remove user accounts.
- Compliance: SSO can help your organization to comply with regulatory requirements and industry standards related to identity and access management, such as HIPAA, GDPR, and PCI DSS.